【SUCTF2018】dead_z3r0
知识点:pyc隐写、pyc隐写工具stegosaurus(剑龙)
stegosaurus(剑龙) 提取pyc隐写文件。
用法:
|
|
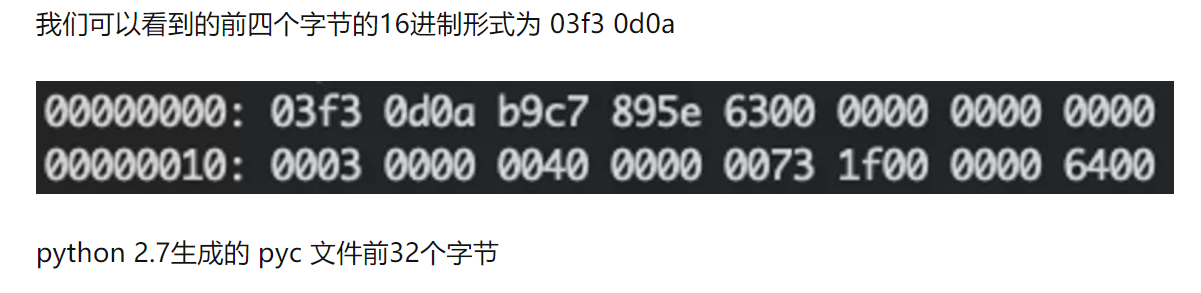
关于pyc文件头的记录:
| python版本 | 文件头magic number 值 |
|---|---|
| python 2.7 | 03 F3 0D 0A |
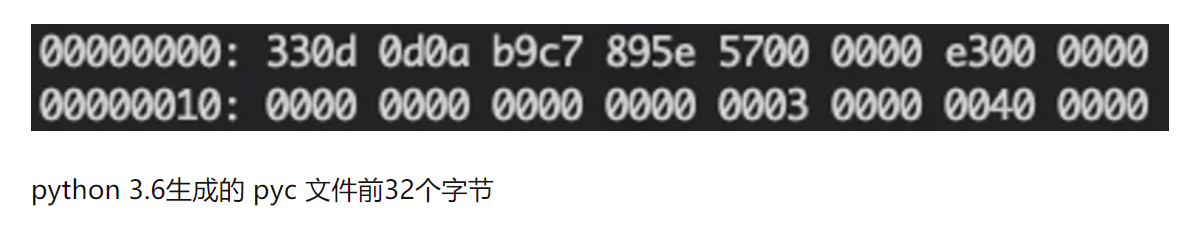
| python 3.6 | 33 0D 0D 0A |
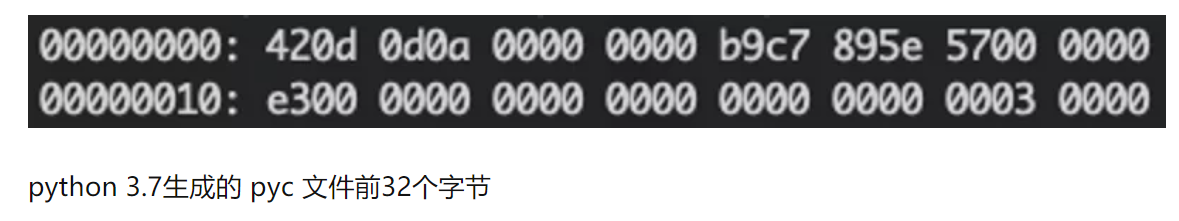
| python3.7 | 42 0D 0D 0A |
| python 3.8 | 55 0D 0D 0A |
pyc 文件的格式:
magic number + 源代码文件信息 + PyCodeObject
- 4个字节的 magic number
- 12个字节的源代码文件信息(不同版本的长度不同)
- 序列化之后的 PyCodeObject
|
|
|
|
|
|
题目分析
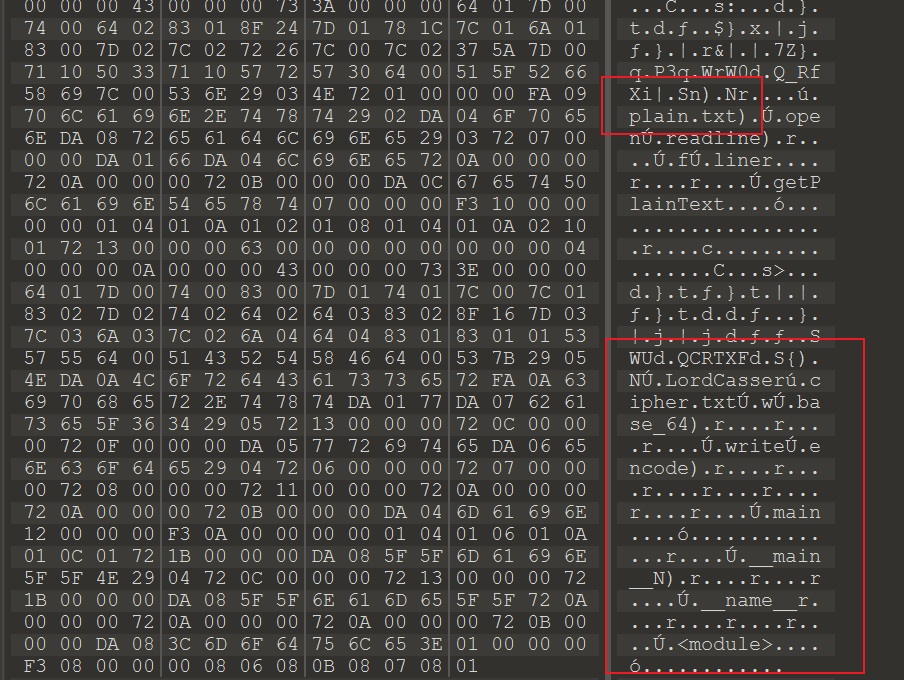
010editor 分析文件,发现开头的文件好像是base64编码,去解密了一下,乱码没啥用。
在后面的一段好像是 pyc 文件,
33 0D 0D 0Apython3.6 的pyc文件头
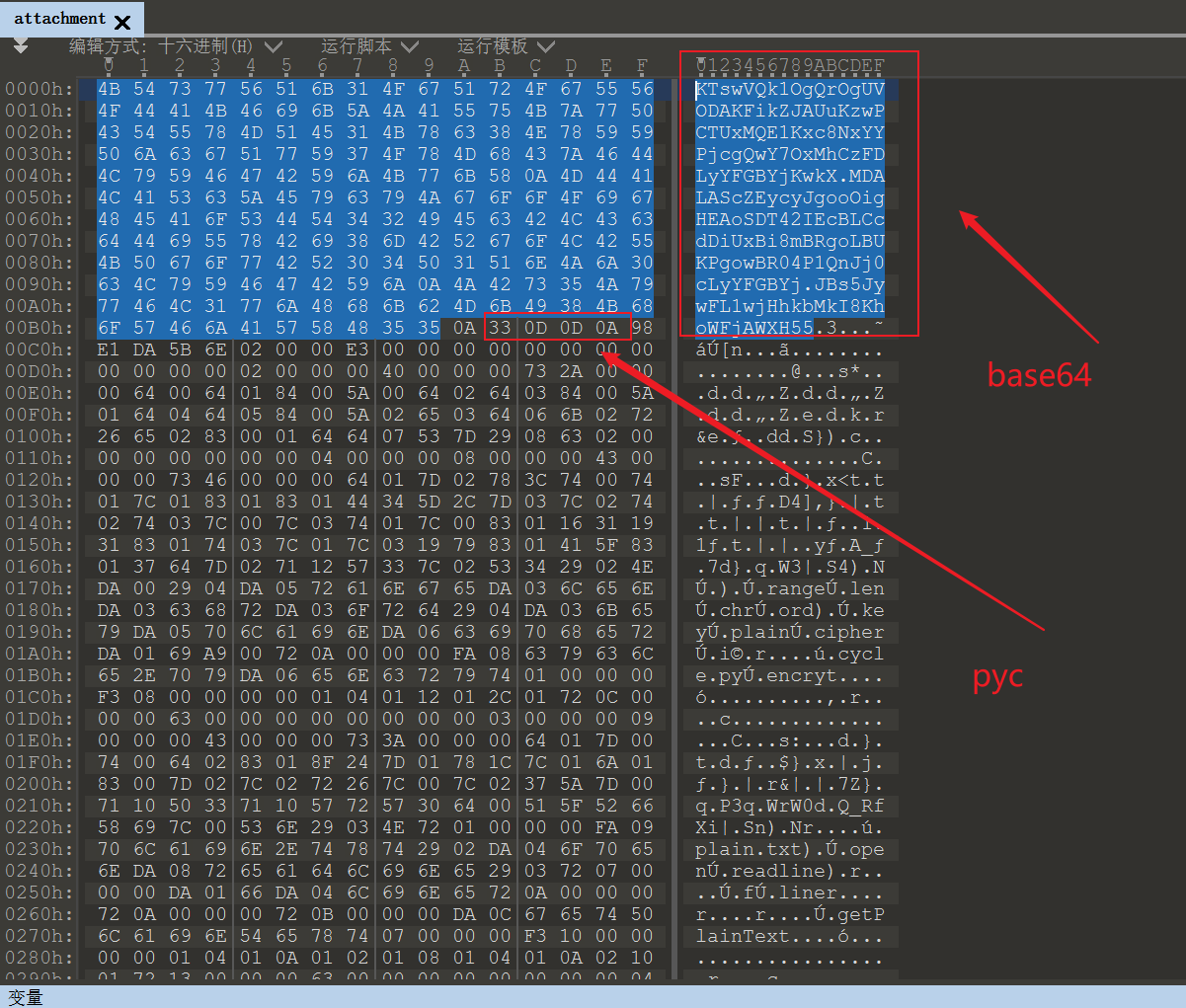
从后面的这段字符串也可以看出这是 python 文件
|
|
接下来就是用 stegosaurus(剑龙) 提取隐写文件。
用法:
|
|

SUCTF{Z3r0_fin411y_d34d}
【XMAN2018排位赛】ppap
知识点:base64解码成图片
题目分析
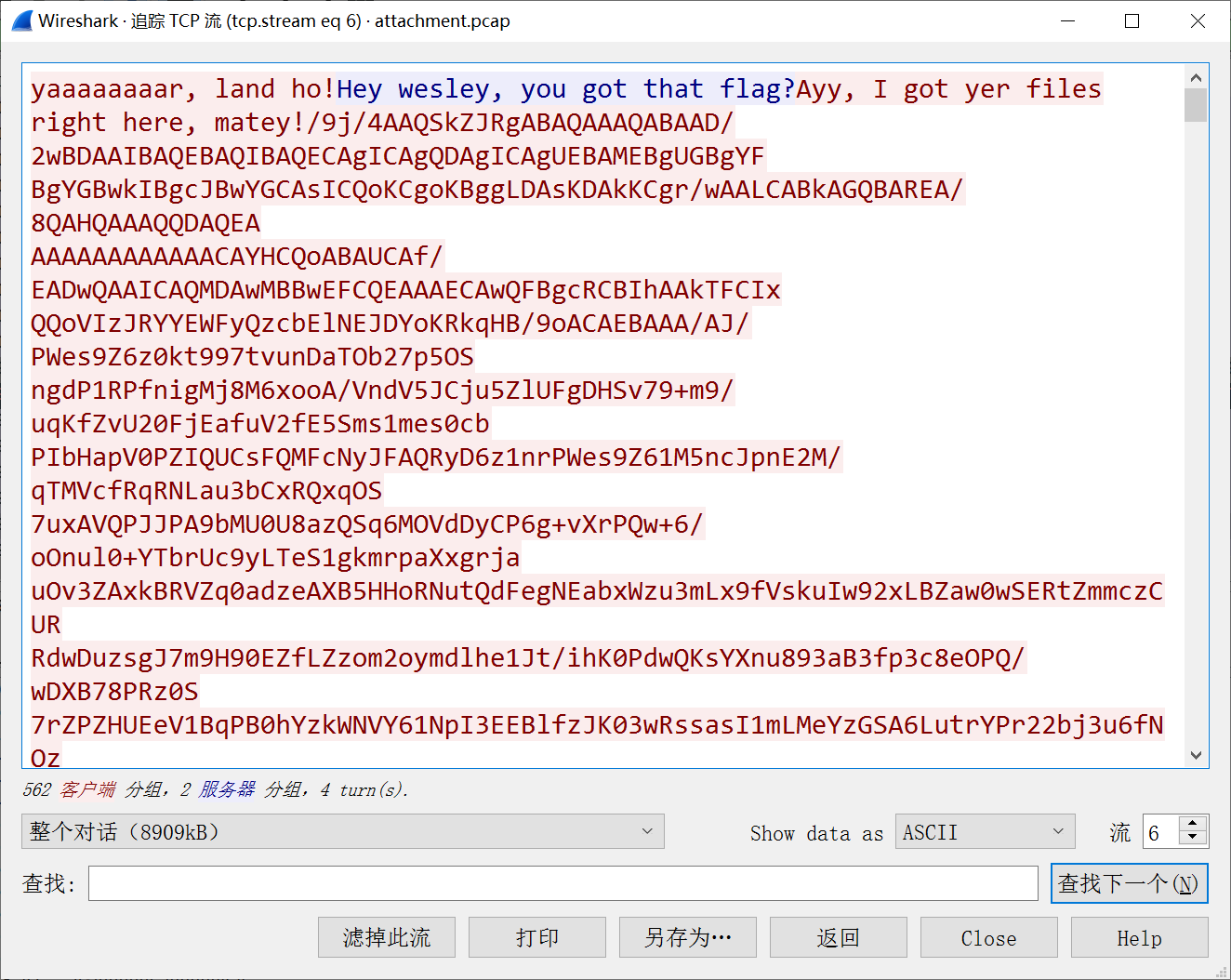
追踪TCP流,找到 flag信息。发现一大串 base64 编码,用在线网站解码
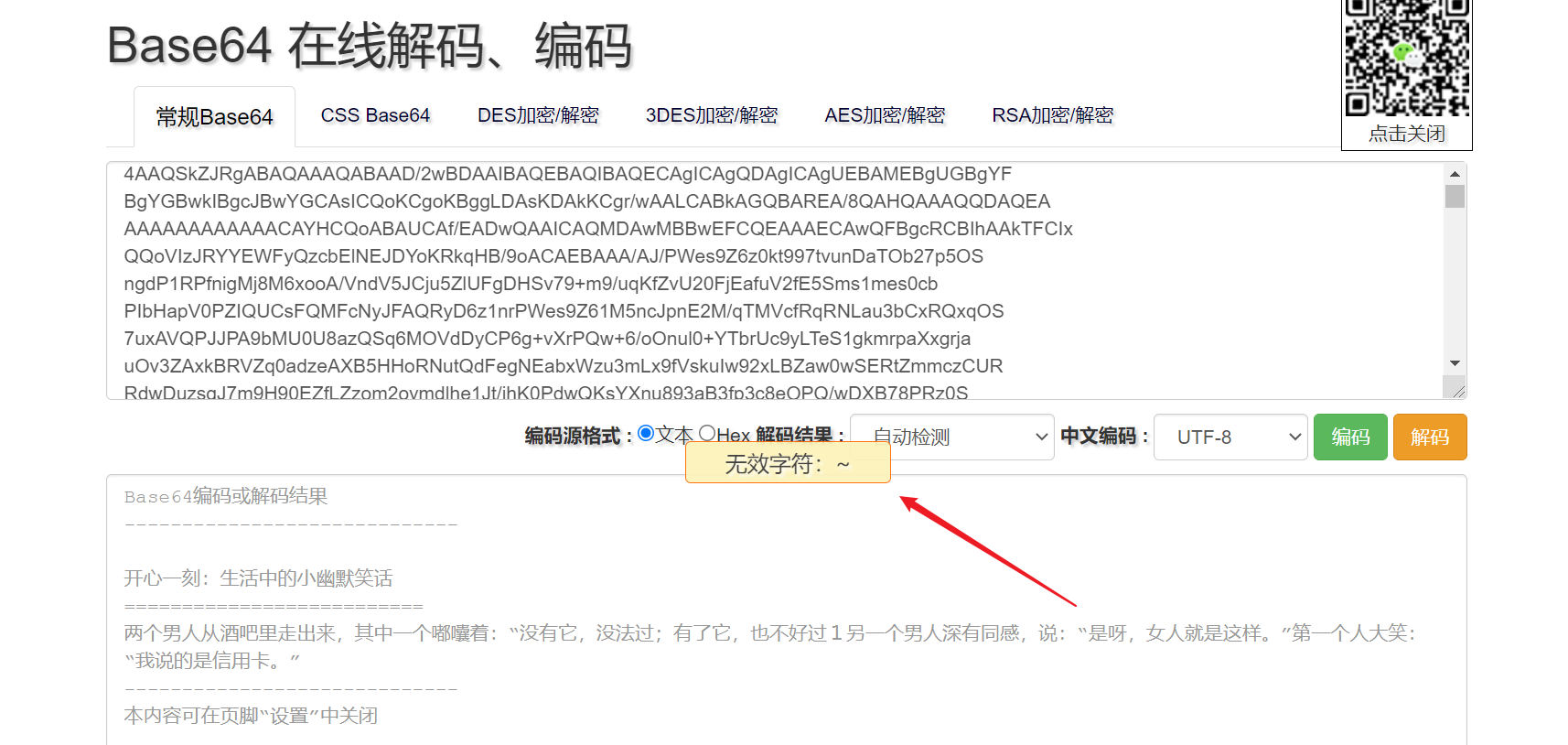
发现无效字符 ~ ,在文本中找一下。
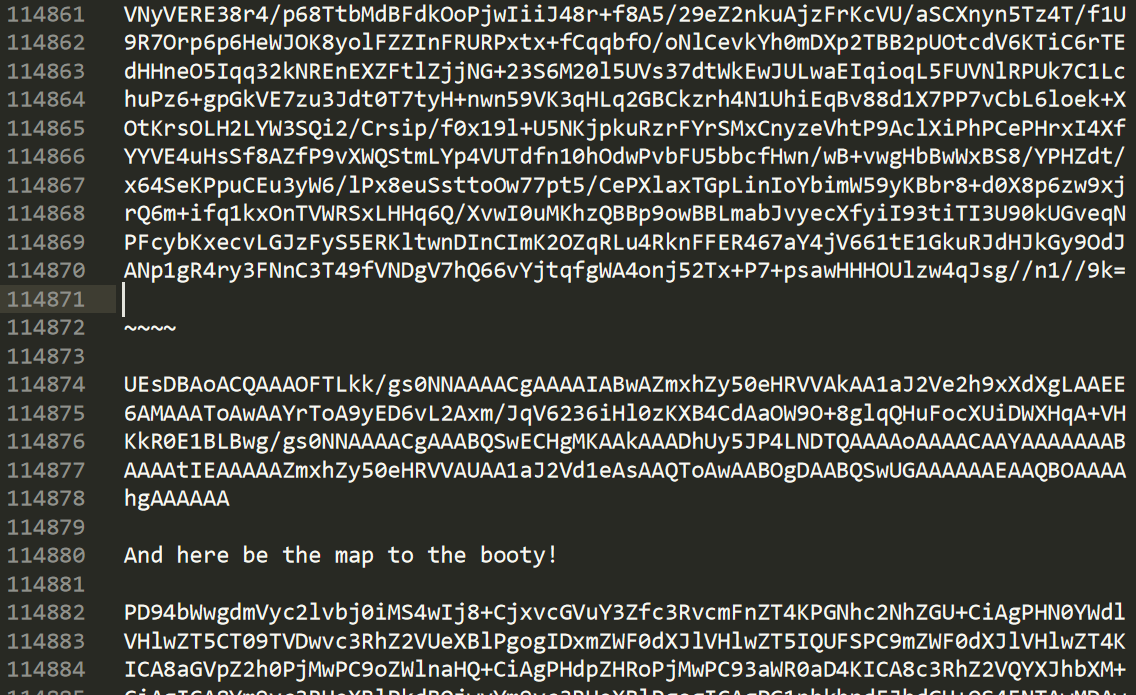
重新解码base64
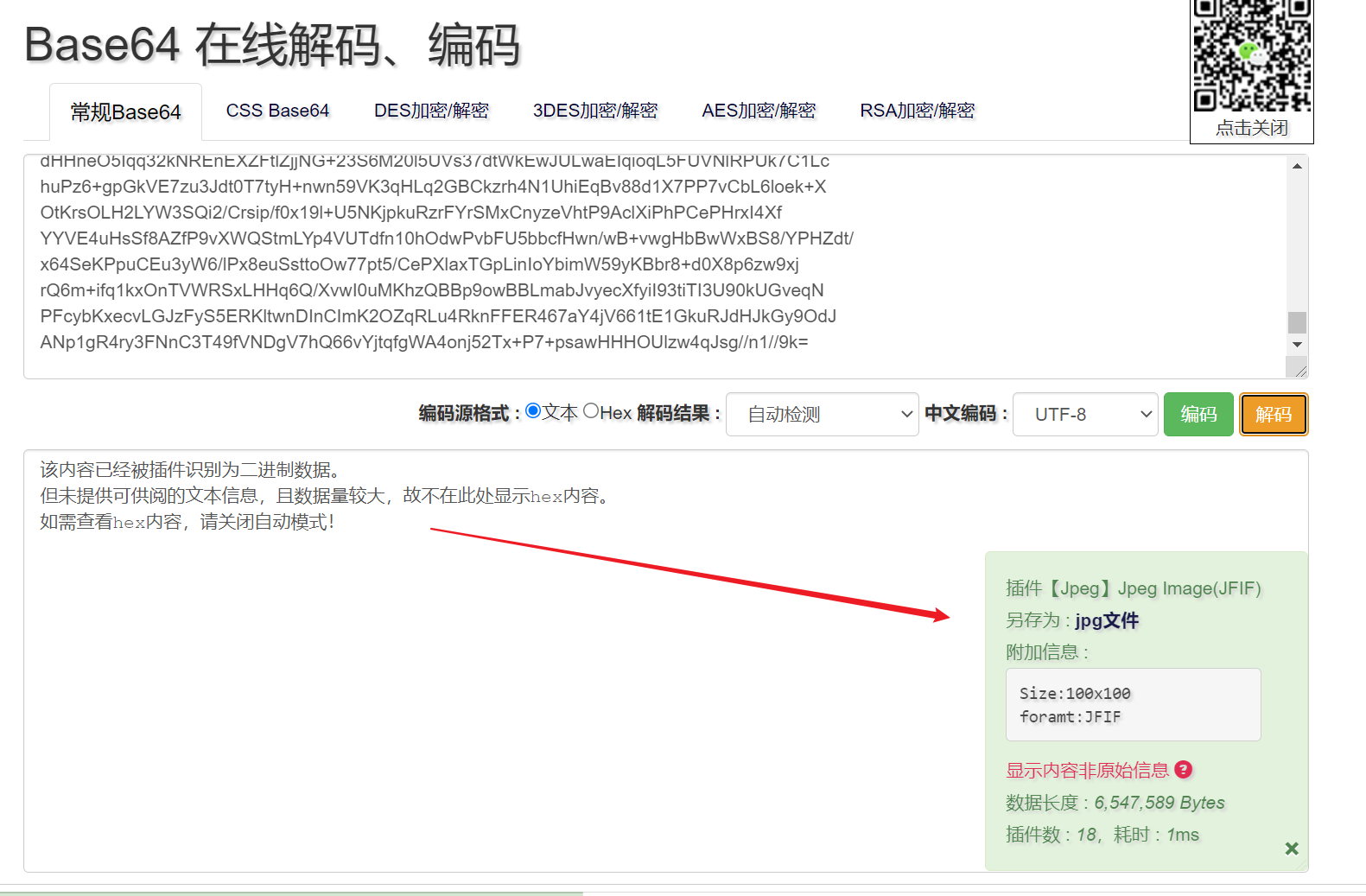
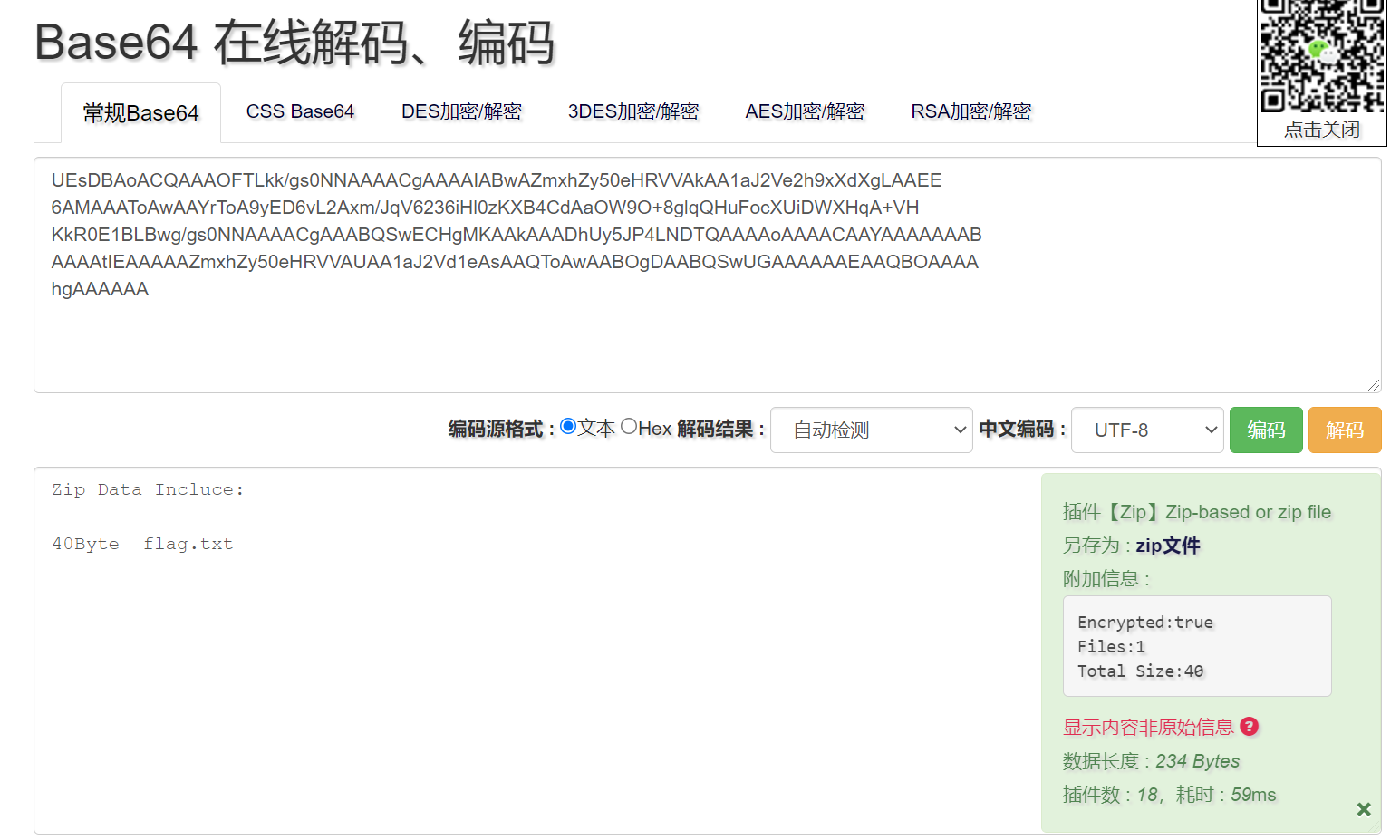
解码后发现,三段分别解码为不同的数据。中间一段为 ZIP,最后一段为 XMl,貌似没啥用。
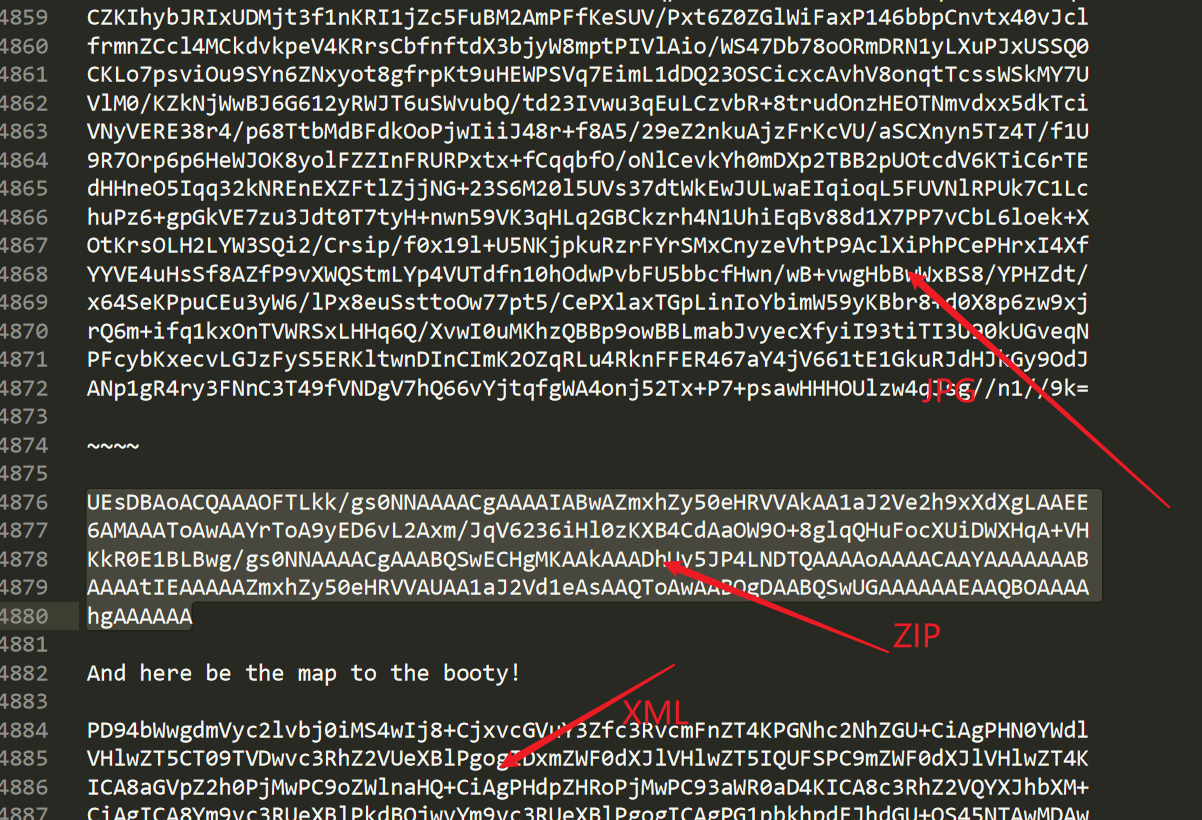
得到的ZIP 文件需要密码
看 ROOT师傅和末初师傅的blog说用 这个网站能解出来。反正我是没搞出来。
https://passwordrecovery.io/zip-file-password-removal/
得到密码:skullandcrossbones
|
|
【BSidesSF2020】barcoder
知识点:手工修复条形码、修图工具GIMP
找了个可以替代PS的修图软件
下载了不会用,这道题还是用的自带的画图软件
题目分析
用 StegSolve 将红色去掉
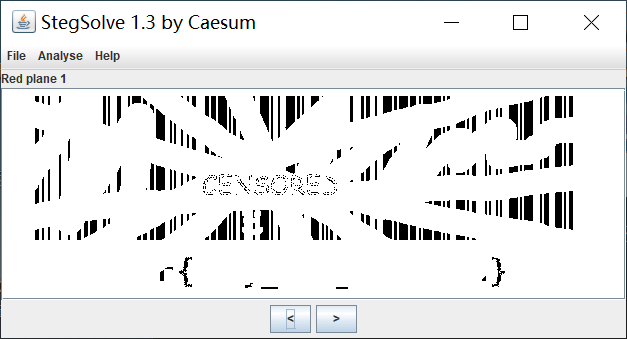
用win10自带的画图一把梭,人都要没了,傻逼。

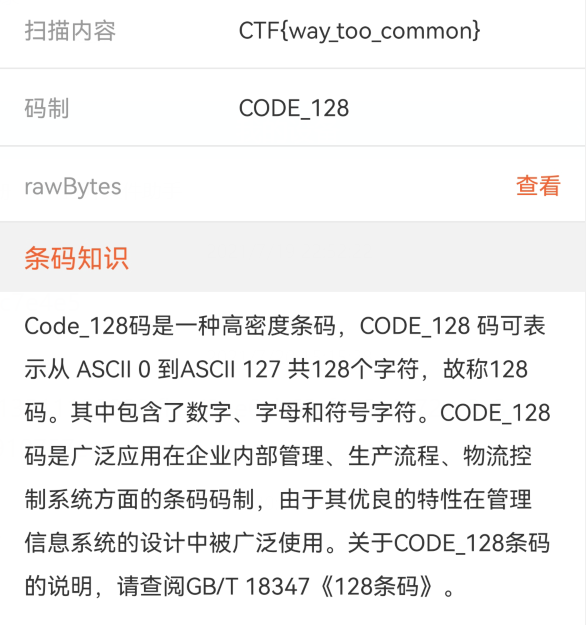
用手机软件,中国编码,扫描得到 flag
CTF{way_too_common}
【INSHack2018】Spreadshit
知识点:Excel隐写
题目分析
用 Excel 打开题目给的 spreadshit.ods 文件,发现一遍空白。根据经验肯定有隐写的内容。
将表格全选,选择菜单栏中的, 表单格式 => 突出显示单元格规则 => 文本包含
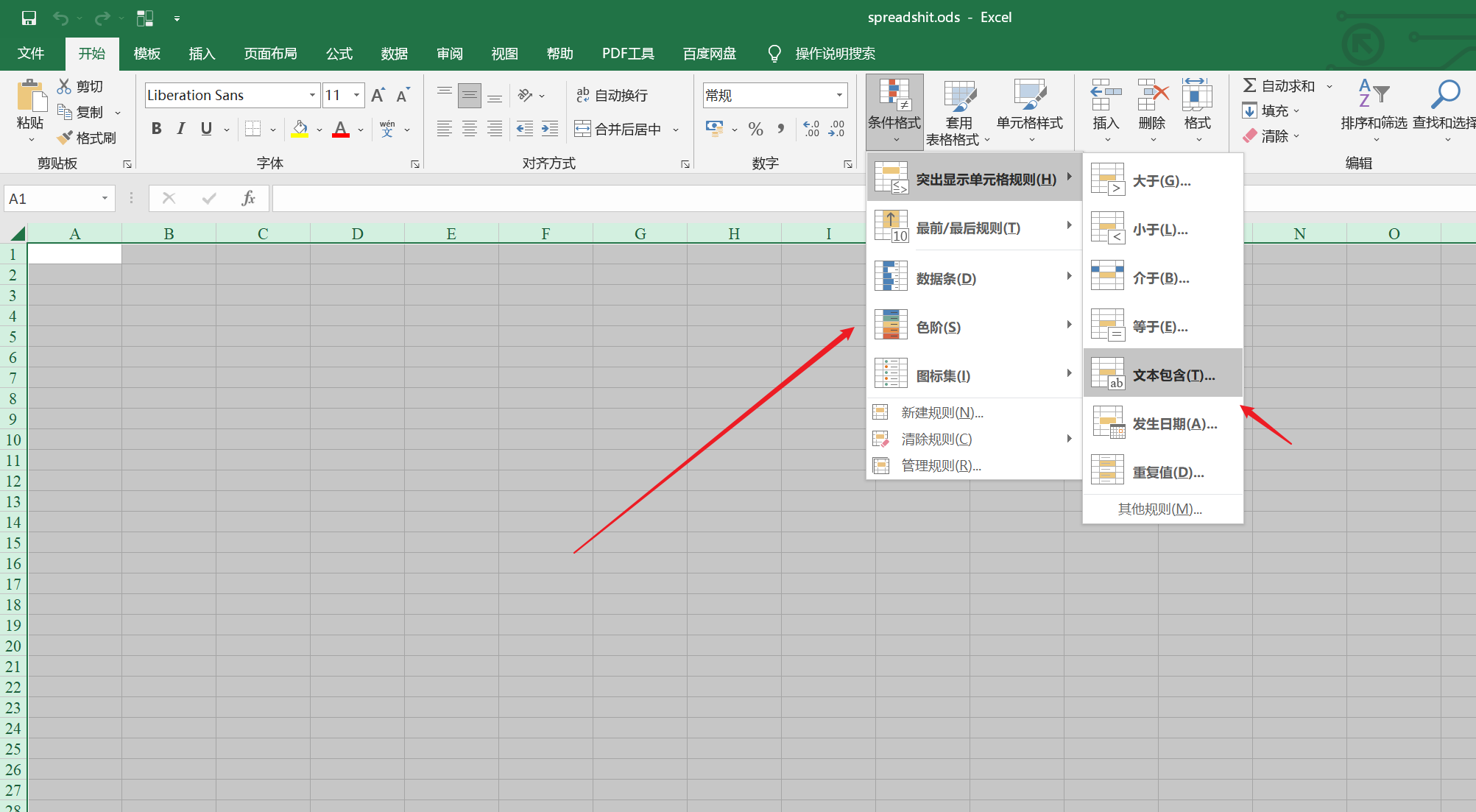
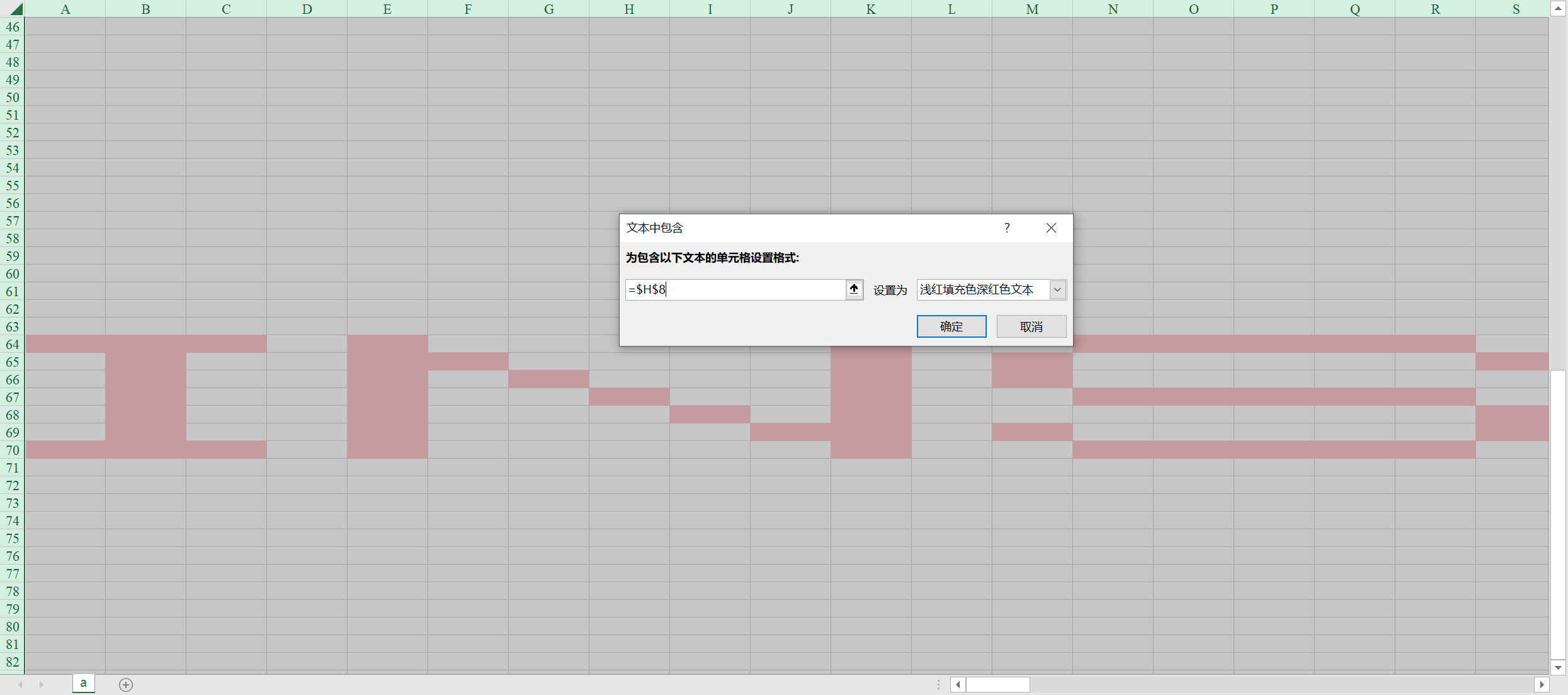
选择规则时在表格上随便点击一下,发现有文本出现

|
|
【GKCTF 2021】FireFox Forensics
知识点:FireFox密码取证
工具:
kali安装 firewd过程:
|
|
题目分析
安装好 firewd 后执行命令
|
|
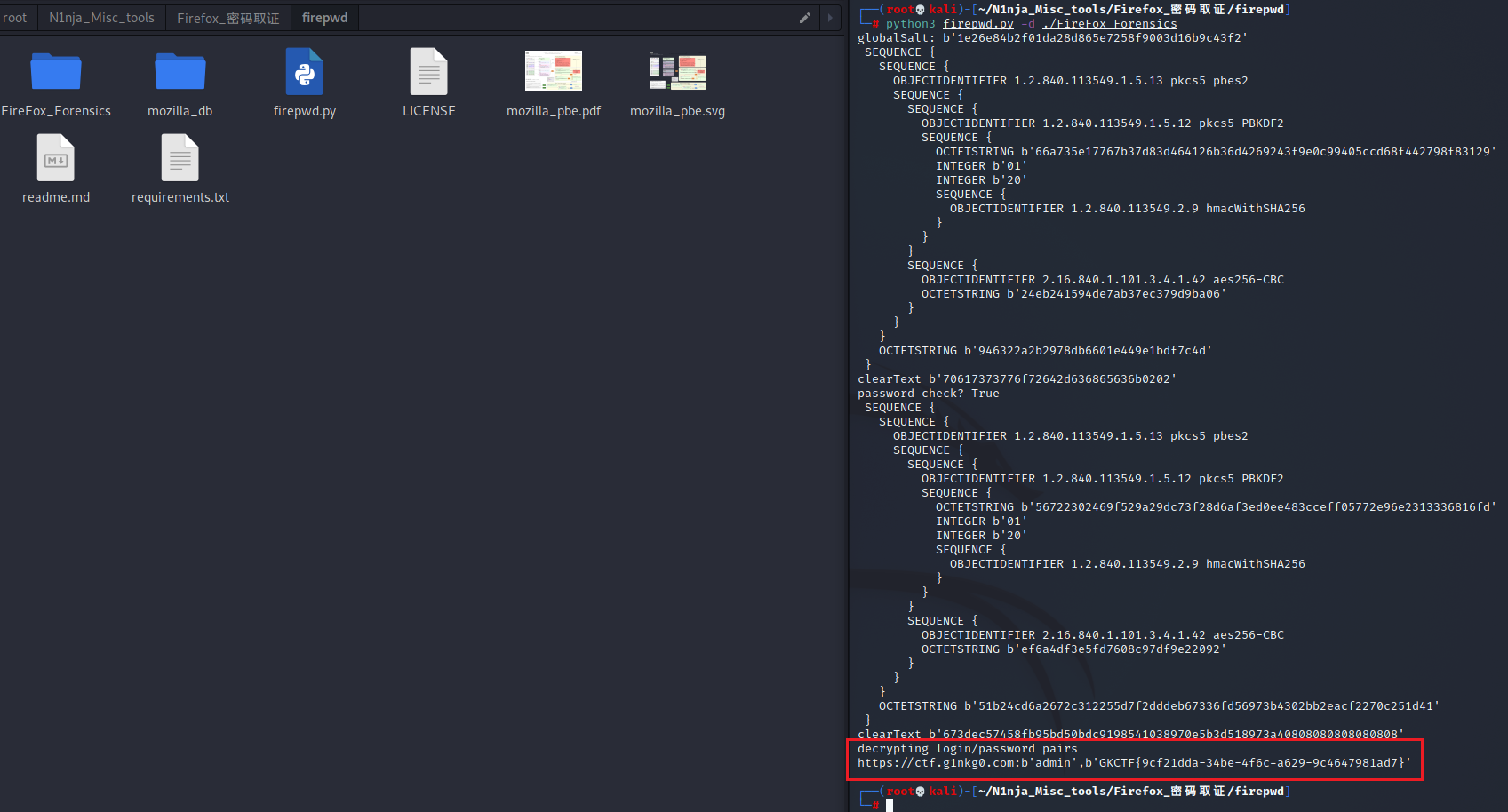
|
|
【RCTF2019】printer
知识点:打印机编程(BITMAP、BAR)
解题EXP:
|
|
题目分析
分析流量发现两个特殊的流量
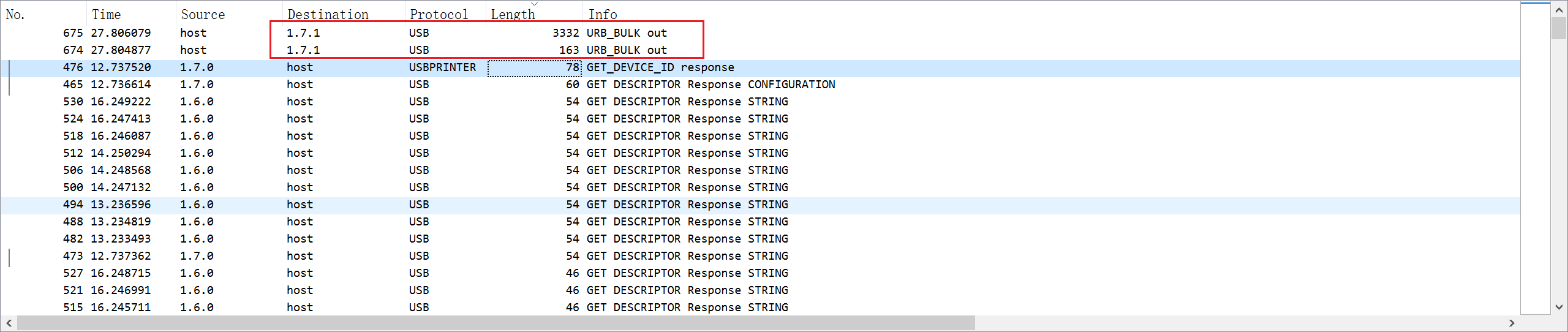
flag{my_tsc_hc3pnikdk}
【QCTF2018】picture
知识点:LSB加密隐写、DES解密
关于LSB隐写介绍:
LSB隐写只适用于 无损压缩(
png) 或 无压缩(bmp)图片
做题技巧:
遇到LSB隐写题目,先通过 zsteg 无参数地检索一遍数据,然后添加
--all参数再检索一遍,最后使用StegSolve
flag以数据的形式存在,zsteg能快速解决;flag以图片的形式存在,只能通过StegSolve逐一查看
StegSolve提供"反色"、"数据提取"、"文件格式"、"帧浏览"、"立体试图"、"图像合成"(双图问题)功能
LSB加密隐写,需要用脚本来提取隐写的数据。(需要知道加密的密码)
|
|
学习文章:
DES解密:
GitHub上的DES解密脚本
|
|
题目分析
拿到题目后,在kali里面用 命令 file 分析,发现是png 文件。添加后缀名,得到png图片。

用binwalk、foremost分析后,发现没有提取出有效文件
那么对于 PNG图片,最大的可能就是 LSB隐写了。LSB隐写是专门针对 png和bmp这种 无损压缩或者无压缩的文件进行的隐写
用工具 Zsteg 进行提取分析,也没有得到有效的文件
|
|
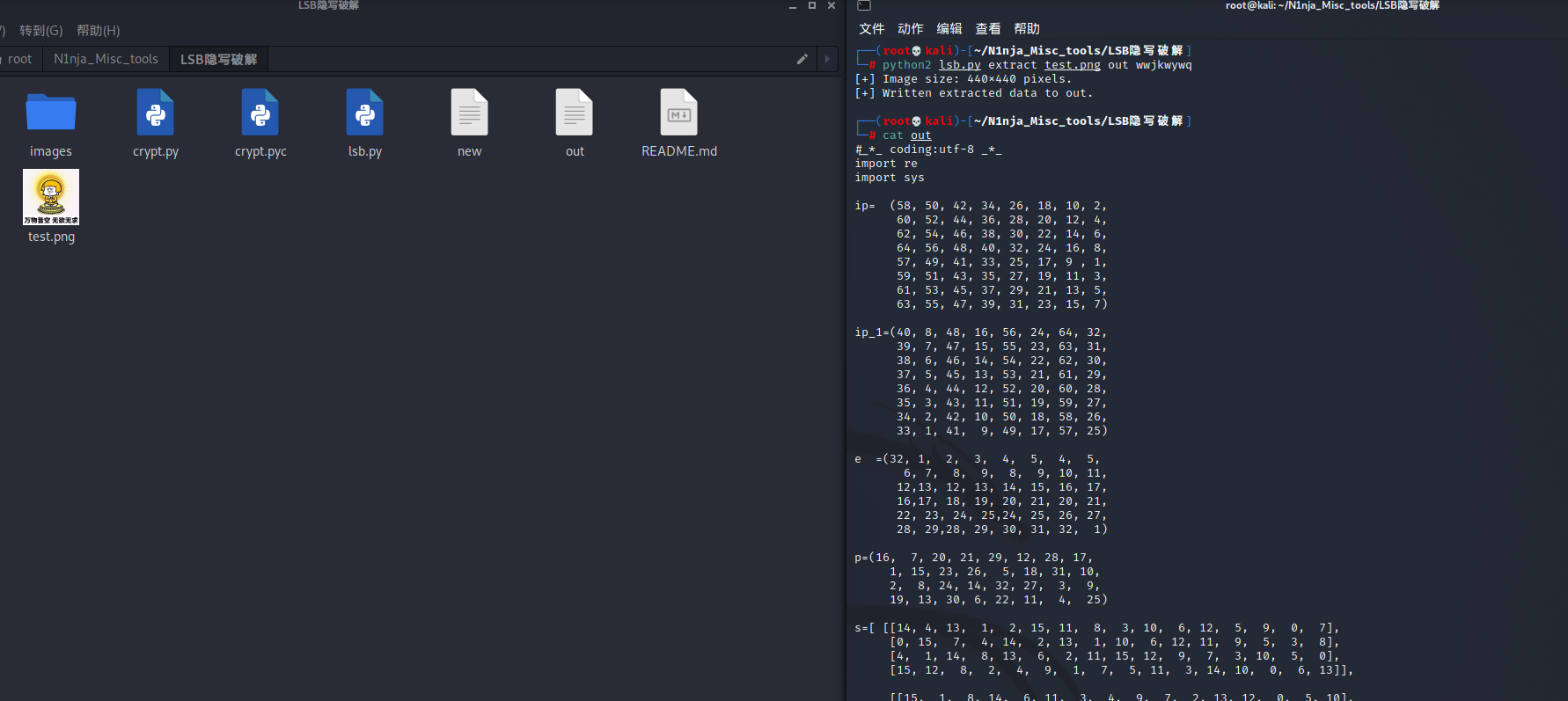
尝试 LSB加密隐写的破解
|
|
关于密码,看了wp才知道是
万物皆空,无欲无求的首字母缩写 wwjkwywq
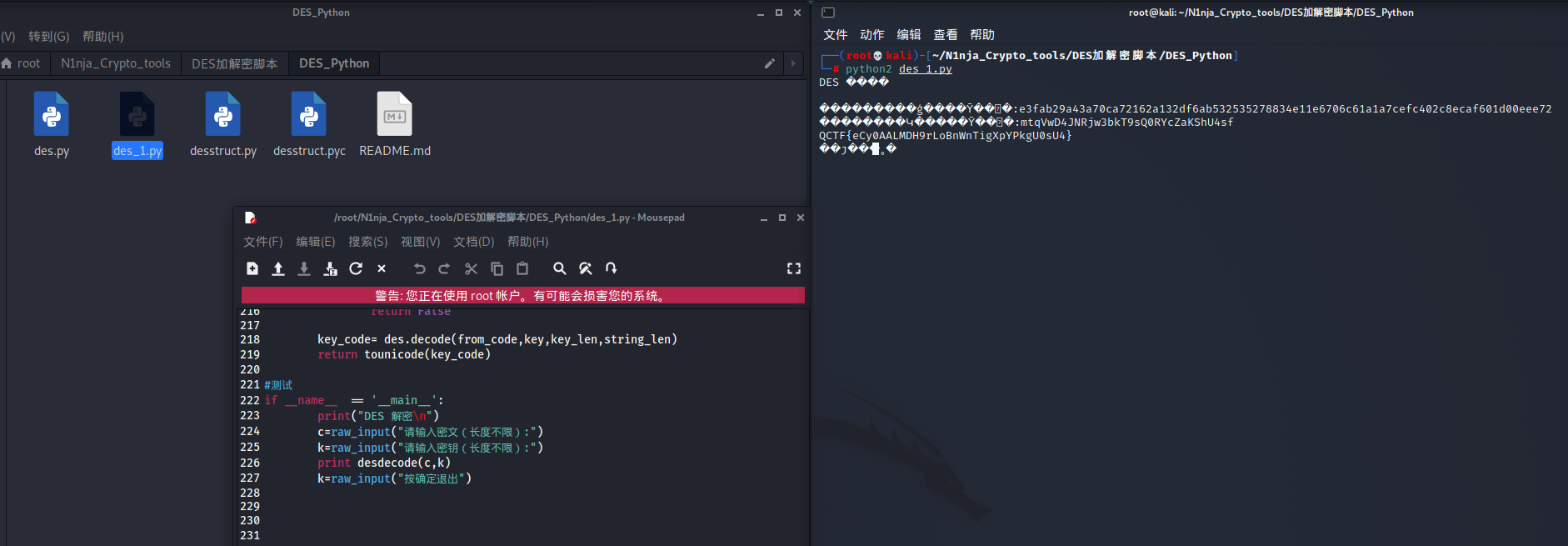
拿到一份 进行DES加密相关的代码
|
|
GitHub上的DES解密脚本
|
|
|
|
【watevrCTF 2019】Polly
知识点:数学公式计算
题目分析
|
|
注意这里数学计算量太大,为了精确计算,建议使用 sagemath 或者使用python的 sympy 库
|
|
【INSHack2019】Passthru
知识点:流量分析(TLS)、sslkey.log对称密钥
题目分析
百度了一下 sslkey.log 文件,知道他是用于 TLS加密通信过程中的 对称密钥。
使用sslkey解密包内容,编辑>首选项>Protocols>TLS
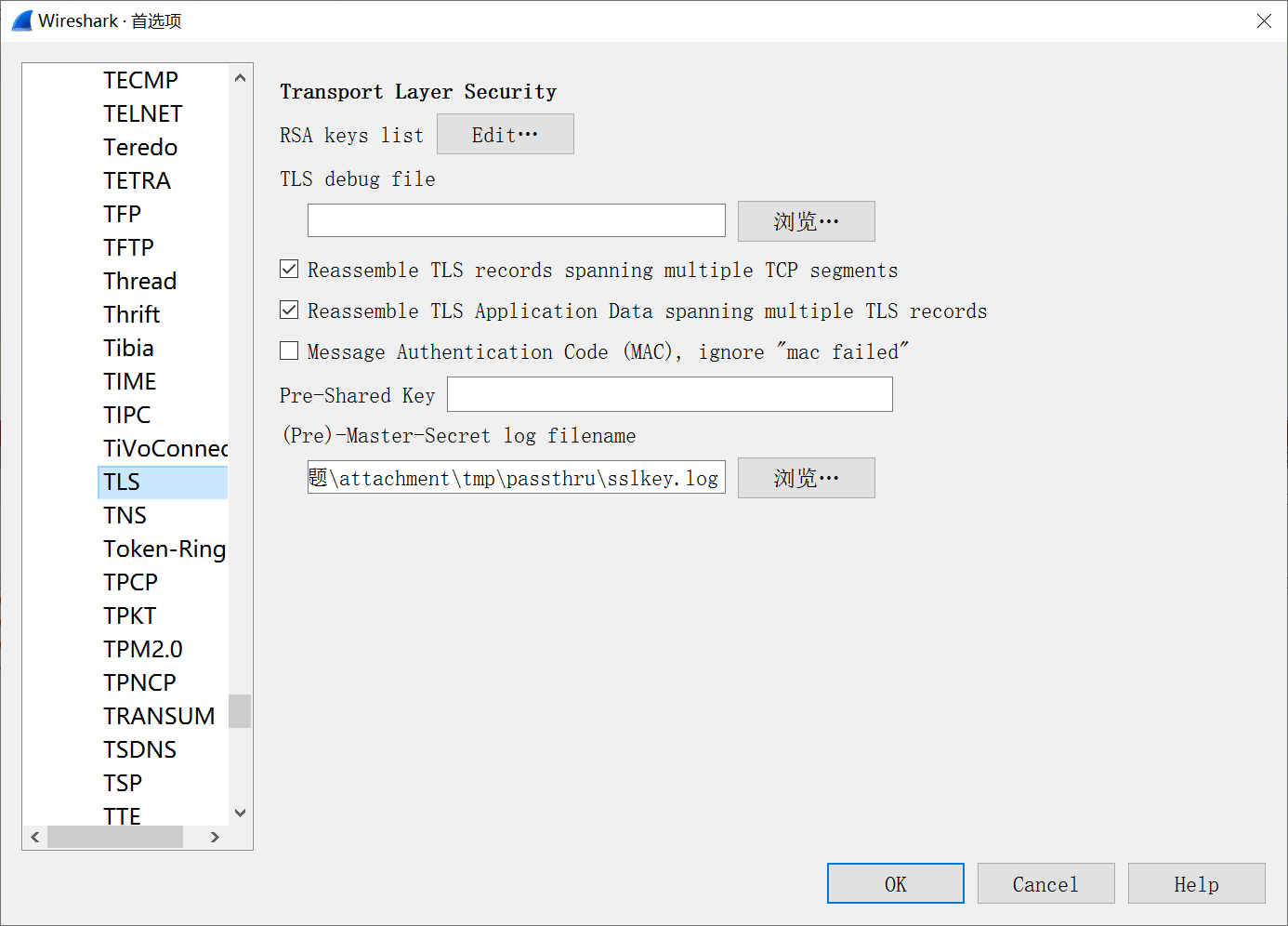
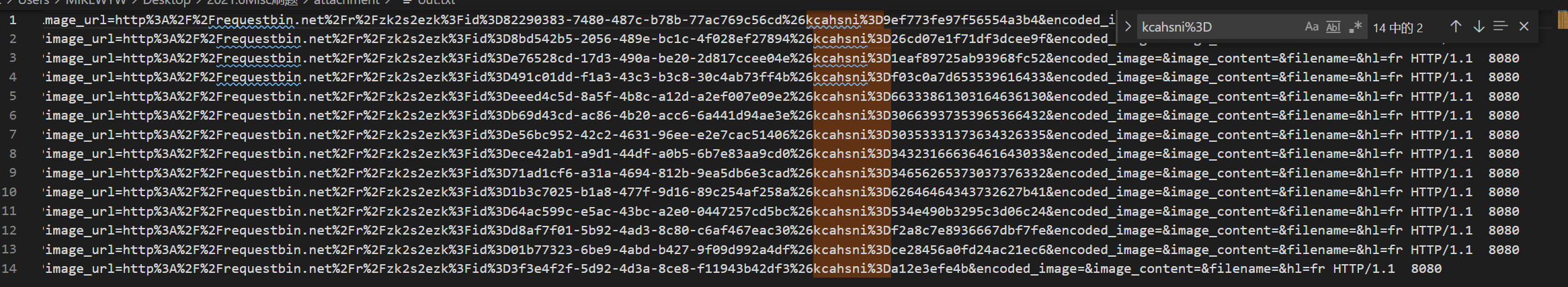
追踪HTTP流,发现在 get请求里有可疑字符 , kcahsni,逆序后不就是 inshack嘛 。
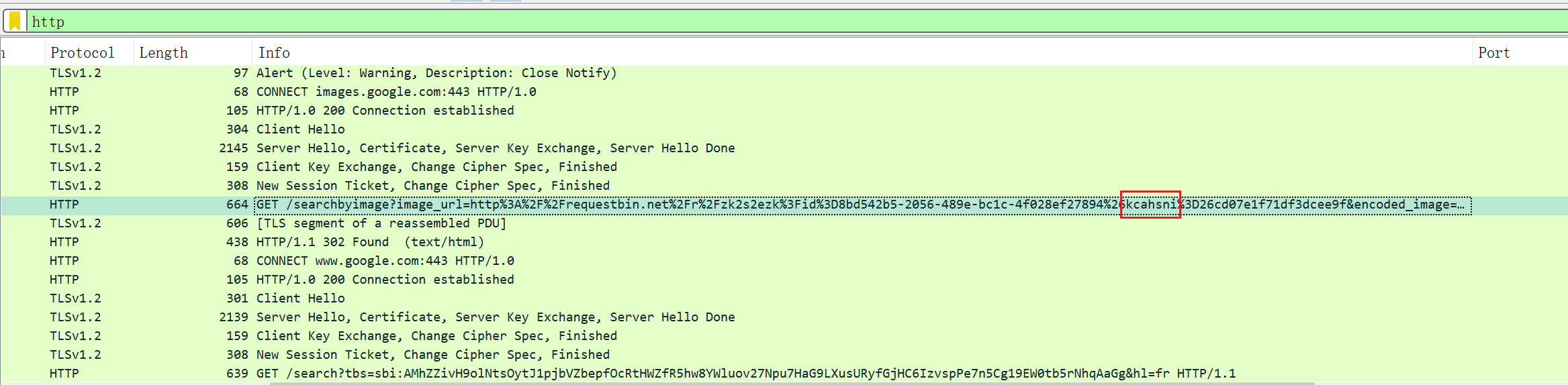
|
|
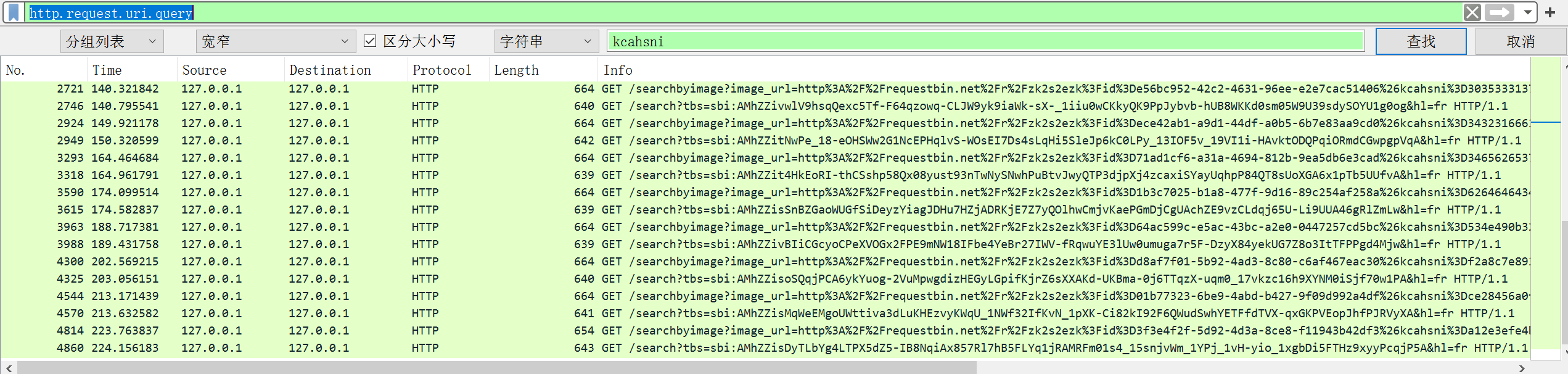
然后文件 → 导出分组解析结果 → 为纯文本,将这些流量包数据提取出来,再用strings命令将与
kcahsni有关的数据提取出来
|
|
对提取的文本进行分析,可知 kcahsni 后面都有一串 16进制编码。
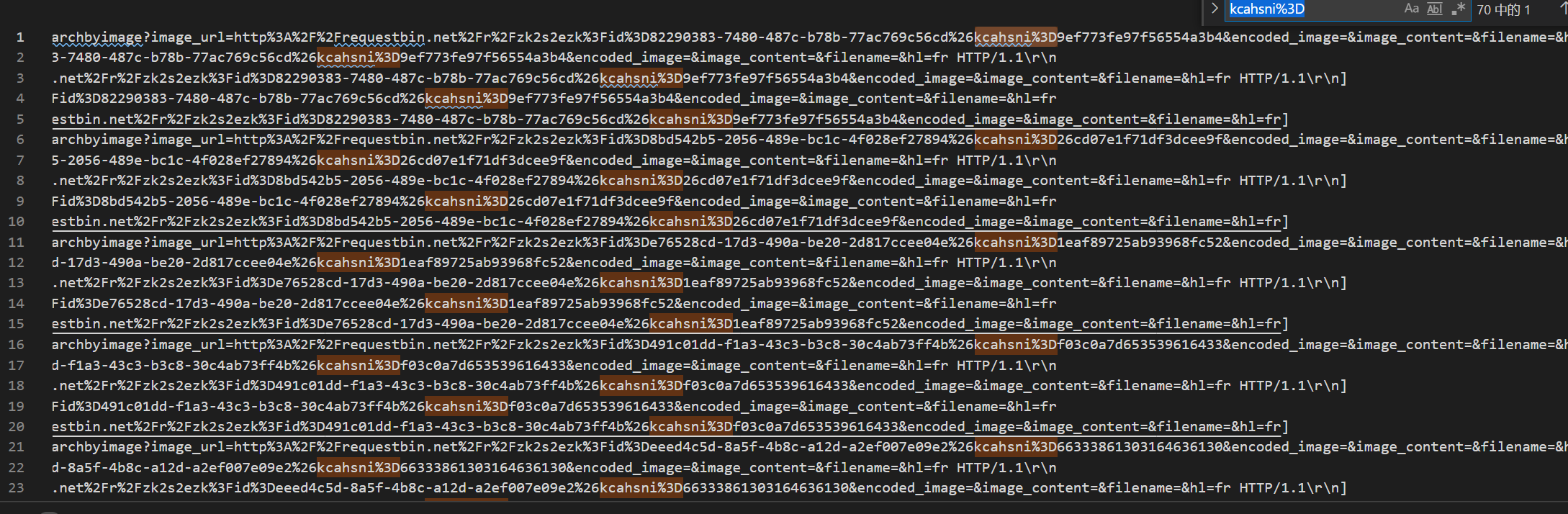
对重复的数据进行整理得到:
|
|
INSA{b274dddb2c7707ebe430dadcf1245c246713502d6e9579f00acd10a83f3da95e}
【[WMCTF2020】行为艺术
知识点:png图片修复、CRC32校验、CyberChef解压zip文件
题目分析
这个题又学到了解题的新姿势
用 CyberChef解压zip文件 ,可以绕过伪加密
打开题目给到 png 文件,010 editor 打开执行 png 模块。提示 CRC 的值不对。
用脚本恢复图片的宽和高:
|
|
修复完得到下面的图片

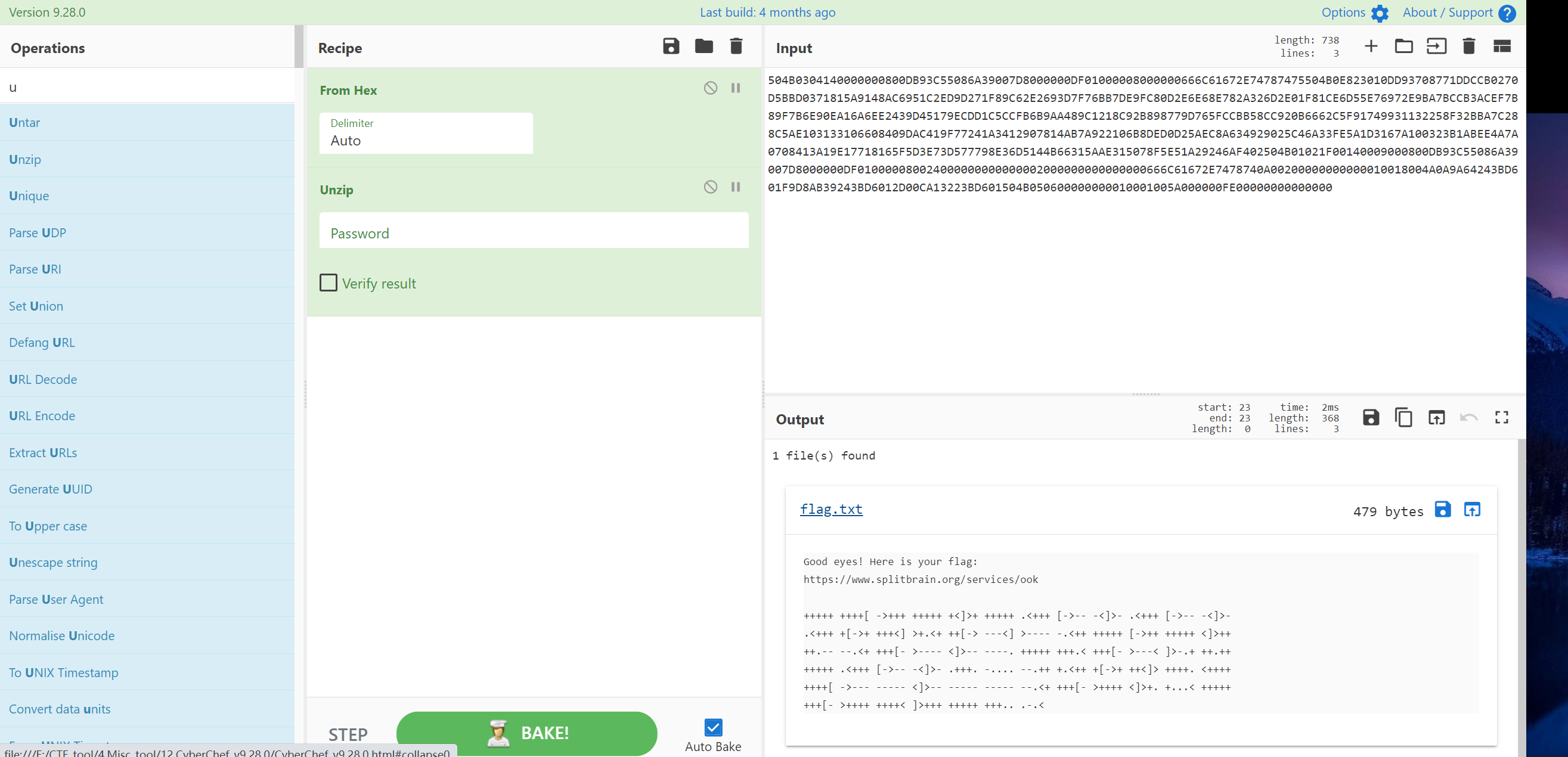
可以看出图片中包含一个压缩包文件,将字符提出来得到:
504B0304140000000800DB93C55086A39007D8000000DF01000008000000666C61672E74787475504B0E823010DD93708771DDCCB0270D5BBD0371815A9148AC6951C2ED9D271F89C62E2693D7F76BB7DE9FC80D2E6E68E782A326D2E01F81CE6D55E76972E9BA7BCCB3ACEF7B89F7B6E90EA16A6EE2439D45179ECDD1C5CCFB6B9AA489C1218C92B898779D765FCCBB58CC920B6662C5F91749931132258F32BBA7C288C5AE103133106608409DAC419F77241A3412907814AB7A922106B8DED0D25AEC8A634929025C46A33FE5A1D3167A100323B1ABEE4A7A0708413A19E17718165F5D3E73D577798E36D5144B66315AAE315078F5E51A29246AF402504B01021F00140009000800DB93C55086A39007D8000000DF010000080024000000000000002000000000000000666C61672E7478740A00200000000000010018004A0A9A64243BD601F9D8AB39243BD6012D00CA13223BD601504B050600000000010001005A000000FE00000000000000
用 CyberChef解压zip文件
+++++ ++++[ ->+++ +++++ +<]>+ +++++ .<+++ [->-- -<]>- .<+++ [->-- -<]>-
.<+++ +[->+ +++<] >+.<+ ++[-> ---<] >---- -.<++ +++++ [->++ +++++ <]>++
++.-- --.<+ +++[- >---- <]>-- ----. +++++ +++.< +++[- >---< ]>-.+ ++.++
+++++ .<+++ [->-- -<]>- .+++. -.... --.++ +.<++ +[->+ ++<]> ++++. <++++
++++[ ->--- ----- <]>-- ----- ----- --.<+ +++[- >++++ <]>+. +...< +++++
+++[- >++++ ++++< ]>+++ +++++ +++.. .-.<
在线Brainfuck 解密
|
|
Tips:用360解压也可以绕过伪加密